SSO/SAML Setup: Okta
Note: DataGrail only supports connections with SAML v2.0.
Standard Configuration For SSO
This section documents the standard configuration for Okta as an identity provider to support login to the DataGrail app. This configuration requires all users be provisioned directly in DataGrail.
-
Sign in to Okta as an admin.
-
Click on Applications -> Applications in the left-hand menu.
-
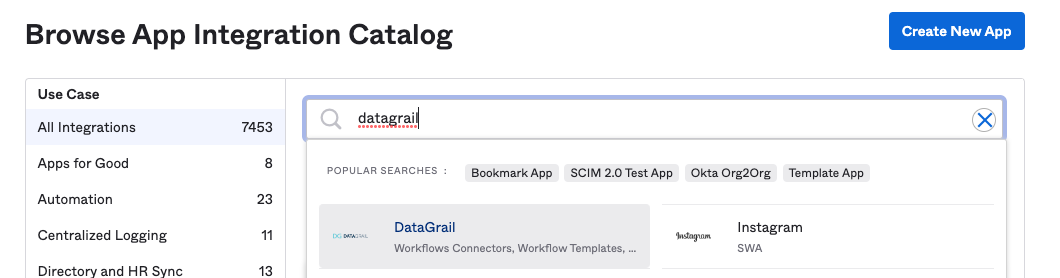
Select Browse App Catalog.
-
Type in ‘DataGrail’ -> Select 'DataGrail' from the dropdown.
-
Select the Add Integration.
-
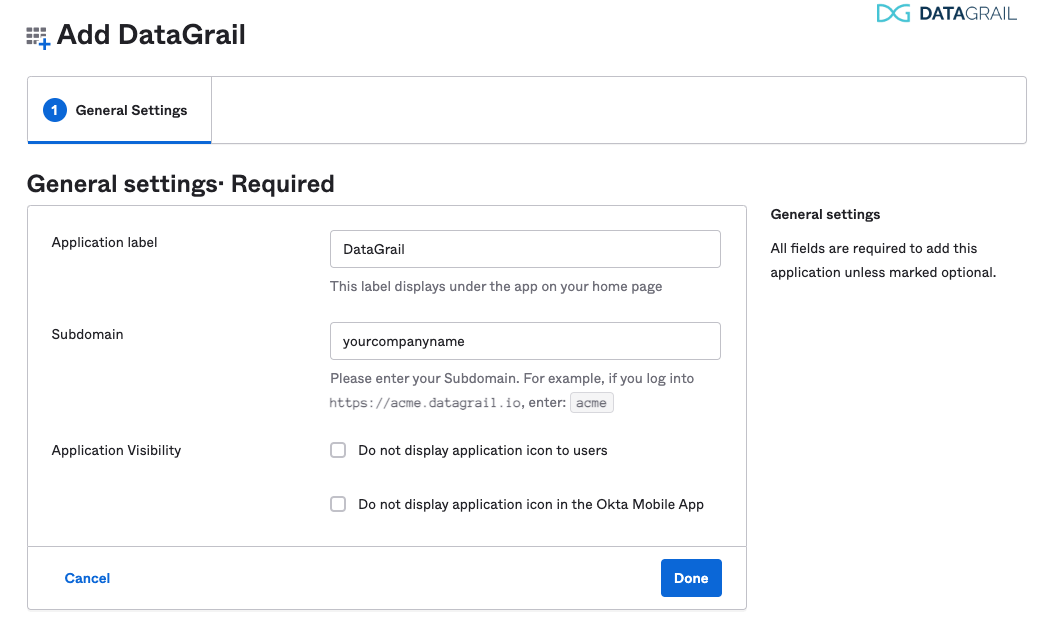
Enter your subdomain.
- If you login to DataGrail at yourcompanyname.datagrail.io, your subdomain would be yourcompanyname; If you are unclear on what your subdomain would be, please confirm with your CSM or reach out to support@datagrail.io.
-
Click on Done button.
-
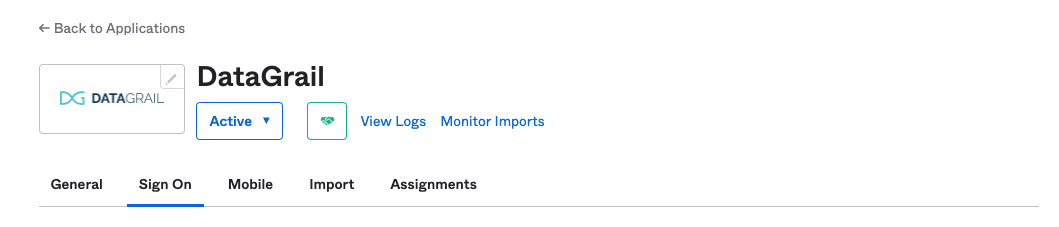
When redirected back to the Applications Page, click on the DataGrail Application and then the Sign On tab.
-
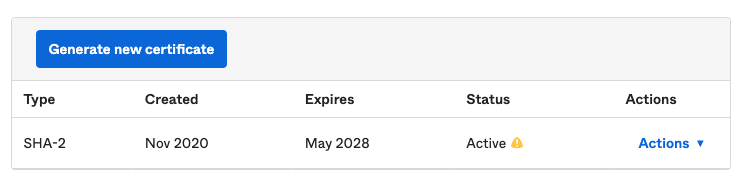
Scroll to SAML Signing Certificates section.
-
You should see an active certificate that is automatically created. This is a signing certificate that will sign the SAML assertions. Click on the Actions dropdown and View IdP Metadata (this should open in another tab).
-
Copy the URL of the Identity Provider Metadata.

-
Send the metadata URL to DataGrail at support@datagrail.io.
Please visit Inviting New Users with Okta for more instructions on adding users and managing roles.
Okta Group Provisioning For SSO
The Group Provisioning functionality is best for advanced users that would like to provision roles automatically based on group assignments within Okta.
Creating the Okta App
-
Sign in to Okta as an admin.
-
Click on Applications -> Applications in the left-hand menu.
-
Select Create App Integration and choose SAML 2.0.
-
Name the app and select next.
-
Enter the SAML Settings:
- Single Sign On URL: https://<DataGrail Subdomain>.datagrail.io/saml/auth
- Audience URI (SP Entity ID): https://<DataGrail Subdomain>.datagrail.io/saml/metadata
- <DataGrail Subdomain> should be replaced with the subdomain configured for your account (i.e. 'newcustomer' for newcustomer.datagrail.io). If you are unclear on what your subdomain would be, please confirm with your CSM or reach out to support@datagrail.io.
-
Select next and create the application.
-
Scroll to SAML Signing Certificates section.
-
You should see an active certificate that is automatically created. This is a signing certificate that will sign the SAML assertions. Click on the Actions dropdown and View IdP Metadata (this should open in another tab)

-
Copy the URL of the Identity Provider Metadata

-
Send the metadata URL to DataGrail at support@datagrail.io.
Determining Group Mappings
In order to utilize the Group Mapping functionality, mappings between the Okta groups and DataGrail roles must be configured on the DataGrail side.
Please review the DataGrail Roles and Permissions and determine what roles you want to associate with your Okta groups. You can have multiple Okta groups map to the same DataGrail role.
Once you have established your mappings, please send them support@datagrail.io to be configured.
Configuring Attribute Statements
Once DataGrail support confirms the mappings have been set, the attribute statements can now be configured within Okta:
-
Navigate back to the Okta app you created in the first section and select the General tab.
-
Select Edit in the SAML Settings section.
-
Select Next to get to the Configure SAML tab. Scroll down to Group Attribute Statements.
-
For each of the mappings you have defined, create a new attribute statement with the name roles and utilize the filters to associate this with the correct group.

-
Additionally, scroll up to Attribute Statements and configure the following attribute statements:
- First Name
- Name: first_name
- Value: user.firstName
- Last Name
- Name: last_name
- Value: user.lastName
- Email
- Name: email
- Value: user.email
- First Name
-
Select Next and save your changes.
Please visit Inviting New Users with Okta for more instructions on adding users and managing roles.
Okta Just-in-Time Provisioning (JIT) For SSO
The Just-in-Time Provisioning functionality is best for advanced users that would like to provision roles on a per-user basis directly in Okta.
Creating the Okta App
-
Sign in to Okta as an admin.
-
Click on Applications -> Applications in the left-hand menu.
-
Select Create App Integration and choose SAML 2.0.
-
Name the app and select next.
-
Enter the SAML Settings:
- Single Sign On URL: https://<DataGrail Subdomain>.datagrail.io/saml/auth
- Audience URI (SP Entity ID): https://<DataGrail Subdomain>.datagrail.io/saml/metadata
- <DataGrail Subdomain> should be replaced with the subdomain configured for your account (i.e. 'newcustomer' for newcustomer.datagrail.io). If you are unclear on what your subdomain would be, please confirm with your CSM or reach out to support@datagrail.io.
-
Select next and create the application.
-
Scroll to SAML Signing Certificates section.
-
You should see an active certificate that is automatically created. This is a signing certificate that will sign the SAML assertions. Click on the Actions dropdown and View IdP Metadata (this should open in another tab)

-
Copy the URL of the Identity Provider Metadata

-
Send the metadata URL to DataGrail at support@datagrail.io. Please inform DataGrail support that you will be utilizing JIT Provisioning, so that it can be enabled on your account.
Configuring The User Profile
In order to use Okta to send roles to DataGrail, a new attribute must be added to your default user profile.
-
In the left-hand menu, select Directory and Profile Editor. Locate and select your default profile.
-
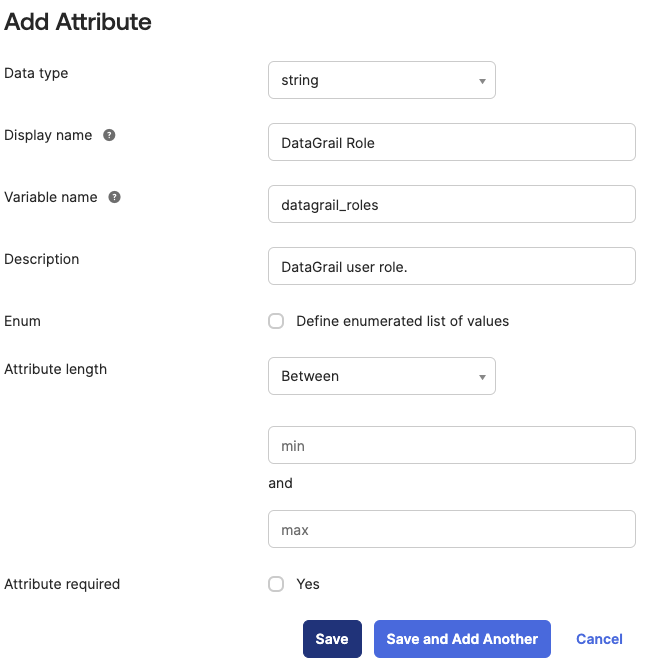
Select Add Attribute and enter the following:
- Data Type: string
- Display Name: DataGrail Role
- Variable Name: datagrail_roles
- Description: DataGrail user role.
- Select save.
Configuring Attribute Statements
-
Navigate back to the Okta app you created in the first section and select the General tab.
-
Select Edit in the SAML Settings section.
-
Select Next to get to the Configure SAML tab. Scroll down to Attribute Statements and configure the following attribute statements:
- First Name
- Name: first_name
- Value: user.firstName
- Last Name
- Name: last_name
- Value: user.lastName
- Email
- Name: email
- Value: user.email
- Roles
- Name: roles
- Value: user.datagrail_roles
- First Name
-
Select Next and save your changes.
Please visit Inviting New Users with Okta for more instructions on adding users and managing roles.
Disclaimer: The information contained in this message does not constitute as legal advice. We would advise seeking professional counsel before acting on or interpreting any material.